
Please know that L&N will never call, text or email you to request your account number, debit card number, PIN, mobile/internet banking log-in, or personal information. We will also never text or email you and request you to release a hold that has been placed on your account for safety purposes. If you receive a similar call, text or email, delete it immediately and call the credit union at (502) 368-5858 or (800) 292-2905 to report it!
Identity Theft
Common Ways Identity Theft Happens
Identity thieves use a variety of methods to steal your personal information, including:
- Dumpster Diving. They rummage through trash looking for bills or other paper with your personal information on it.
- Skimming. They steal credit/debit card numbers by using a special storage device when processing your card.
- Phishing. They pretend to be financial institutions, companies or government agencies, and send email or pop-up messages to get you to reveal your personal information.
- Hacking. They hack into your email or other online accounts to access your personal information, or into a company's database to access its records.
- “Old-Fashioned” Stealing. They steal wallets and purses; mail, including bank and credit card statements; pre-approved credit offers; and new checks or tax information. They steal personnel records from their employers, or bribe employees who have access.
Deter identity thieves by safeguarding your information
- Shred financial documents and paperwork with personal information before you discard them.
- Protect your Social Security number. Do not carry your Social Security card in your wallet or write your Social Security number on a check. Give it out only if absolutely necessary or ask to use another identifier.
- Don’t give out personal information on the phone, through the mail or over the Internet unless you know who you are dealing with. Avoid disclosing personal financial information when using public wireless connections.
- Never click on links sent in unsolicited emails; instead, type in a web address you know. Use firewalls, anti-spyware and anti-virus software to protect your home computer; keep them up-to-date. If you use peer-to-peer file sharing, check the settings to make sure you’re not sharing other sensitive private files. Visit OnGuardOnline.gov for more information.
- Don’t use an obvious password like your birth date, your mother’s maiden name or the last four digits of your Social Security number.
- Keep your personal information in a secure place at home, especially if you have roommates, employ outside help or are having work done in your house.
- Detect suspicious activity by routinely monitoring your financial accounts and billing statements.
Be alert to signs that require immediate attention
- Bills that do not arrive as expected
- Unexpected credit cards or account statements
- Denials of credit for no apparent reason
- Calls or letters about purchases you did not make
- Charges on your financial statements that you don’t recognize
Inspect your credit report
Credit reports contain information about you, including what accounts you have and your bill paying history. The law requires the major nationwide credit reporting companies—Equifax, Experian, and TransUnion—to give you a free copy of your credit report every 12 months if you ask for it. Visit AnnualCreditReport.com or call 1-877-322-8228, a service created by these three companies, to order your free annual credit report. You also can write: Annual Credit Report Request Service, P.O. Box 105281, Atlanta, GA 30348-5281.
If you see accounts or addresses you don’t recognize or information that is inaccurate, contact the credit reporting company and the information provider. To find out how to correct errors on your credit report, visit ftc.gov/idtheft.
Defend against ID theft as soon as you suspect it
Place a “Fraud Alert” on your credit reports, and review the reports carefully. The alert tells creditors to follow certain procedures before they open new accounts in your name or make changes to your existing accounts. The three nationwide consumer reporting companies have toll-free numbers for placing an initial 90-day fraud alert; a call to one company is sufficient.
- Experian: 1-888-EXPERIAN (397-3742)
- TransUnion: 1-800-680-7289
- Equifax: 1-800-525-6285
Placing a fraud alert entitles you to free copies of your credit reports. Look for inquiries from companies you haven’t contacted, accounts you didn’t open and debts on your accounts that you can’t explain.
Contact the security or fraud departments of each company where an account was opened or charged without your consent. Follow up in writing, with copies of supporting documents. Use the ID Theft Affidavit at ftc.gov/idtheft to support your written statement. Ask for verification that the disputed account has been dealt with and the fraudulent debts discharged. Keep copies of documents and records of your conversations about the theft.
File a police report. File a report with law enforcement officials to help you correct your credit report and deal with creditors who may want proof of the crime.
Report the theft to the Federal Trade Commission. Your report helps law enforcement officials across the country in their investigations.
Online: ftc.gov/idtheft
By phone: 1-877-ID-THEFT (438-4338) or TTY, 1-866-653-4261
By mail: Identity Theft Clearinghouse, Federal Trade Commission, Washington, DC 20580
Resources: ftc.gov
Phishing
When internet fraudsters impersonate a business to trick you into giving out your personal information, it’s called phishing. Don't reply to email, text, or pop-up messages that ask for your personal or financial information. Don’t click on links within them either – even if the message seems to be from an organization you trust. It isn’t. Legitimate businesses don’t ask you to send sensitive information through insecure channels.
Examples of Phishing Messages
You open an email or text, and see a message like this:
- "We suspect an unauthorized transaction on your account. To ensure that your account is not compromised, please click the link below and confirm your identity."
- "During our regular verification of accounts, we couldn't verify your information. Please click here to update and verify your information."
- “Our records indicate that your account was overcharged. You must call us within 7 days to receive your refund.”
- The senders are phishing for your information so they can use it to commit fraud.
How to Deal with Phishing Scams
- Delete email and text messages that ask you to confirm or provide personal information (credit card and bank account numbers, Social Security numbers, passwords, etc.). Legitimate companies don't ask for this information via email or text.
- The messages may appear to be from organizations you do business with – banks, for example. They might threaten to close your account or take other action if you don’t respond.
- Don’t reply, and don’t click on links or call phone numbers provided in the message. These messages direct you to spoof sites – sites that look real but whose purpose is to steal your information so a scammer can run up bills or commit crimes in your name.
- Area codes can be misleading as well. Some scammers ask you to call a phone number to update your account or access a "refund." But a local area code doesn’t guarantee that the caller is local.
- If you are concerned about your account or need to reach a financial organization, call the number on your financial statements or on the back of your credit card.
Action Steps
There are steps you can take to avoid a phishing attack.
- Use trusted security software and set it to update automatically.
- Do not email personal or financial information. Email is not a secure method of transmitting personal information.
- Only provide personal or financial information through an organization's website if you type in the web address yourself and if you see signals that the site is secure, like a URL that begins with https (the "s" stands for secure).
- Unfortunately, no indicator is foolproof; some phishers have forged security icons.
- Review credit card and bank account statements as soon as you receive them to check for unauthorized charges. If your statement is late by more than a couple of days, call to confirm your billing address and account balances.
- Be cautious about opening attachments and downloading files from emails, regardless of who sent them. These files can contain viruses or other malware that can weaken your computer's security.
Report Phishing Emails
Forward phishing emails to spam@uce.gov – and to the company, bank, or organization impersonated in the email.
You also may report phishing email to reportphishing@antiphishing.org.
If you are a victim of a phishing email
- File a report with the Federal Trade Commission at www.ftc.gov/complaint.
- Visit the FTC’s Identity Theft website. Victims of phishing could become victims of identity theft. There are steps you can take to minimize your risk.
Resources: OnGuardOnline.gov
Malware
Malware is short for “malicious software." It includes viruses and spyware that get installed on your computer, phone, or mobile device without your consent. These programs can cause your device to crash and can be used to monitor and control your online activity. Criminals use malware to steal personal information, send spam, and commit fraud.
Avoid Malware
Scam artists try to trick people into clicking on links that will download malware and spyware to their computers, especially computers that don't use adequate security software. To reduce your risk of downloading unwanted malware and spyware:
- Keep your security software updated. At a minimum, your computer should have anti-virus and anti-spyware software, and a firewall. Set your security software, internet browser, and operating system (like Windows or Mac OS) to update automatically.
- Don't click on any links or open any attachments in emails unless you know who sent it and what it is. Clicking on links and opening attachments – even in emails that seem to be from friends or family – can install malware on your computer.
- Download and install software only from websites you know and trust. Downloading free games, file-sharing programs, and customized toolbars may sound appealing, but free software can come with malware.
- Minimize "drive-by" downloads. Make sure your browser security setting is high enough to detect unauthorized downloads. For Internet Explorer, for example, use the "medium" setting at a minimum.
- Use a pop-up blocker and don't click on any links within pop-ups. If you do, you may install malware on your computer. Close pop-up windows by clicking on the "X" in the title bar.
- Resist buying software in response to unexpected pop-up messages or emails, especially ads that claim to have scanned your computer and detected malware. That's a tactic scammers use to spread malware.
- Talk about safe computing. Tell your kids that some online actions can put the computer at risk: clicking on pop-ups, downloading "free" games or programs, opening chain emails, or posting personal information.
- Back up your data regularly. Whether it's text files or photos that are important to you, back up any data that you'd want to keep in case your computer crashes.
Detect Malware
Monitor your computer for unusual behavior. Your computer may be infected with malware if it:
- slows down, crashes, or displays repeated error messages
- won't shut down or restart
- serves up a barrage of pop-ups
- displays web pages you didn't intend to visit, or sends emails you didn't write
Other warning signs of malware include
- new and unexpected toolbars
- new and unexpected icons in your shortcuts or on your desktop
- a sudden or repeated change in your computer's internet home page
- a laptop battery that drains more quickly than it should
Get Rid of Malware
- If you suspect there is malware is on your computer, take these steps:
- Stop shopping, banking, and doing other online activities that involve user names, passwords, or other sensitive information.
- Update your security software, and then run it to scan your computer for viruses and spyware. Delete anything it identifies as a problem. You may have to restart your computer for the changes to take effect.
- If your computer is covered by a warranty that offers free tech support, contact the manufacturer. Before you call, write down the model and serial number of your computer, the name of any software you've installed, and a short description of the problem.
- Many companies – including some affiliated with retail stores – offer tech support on the phone, online, at their store, and in your home. Decide which is most convenient for you. Telephone and online help generally are the least expensive, but you may have to do some of the work yourself. Taking your computer to a store usually is less expensive than hiring a repair person to come into your home.
- Once your computer is back up and running, think about how malware could have been downloaded to your machine, and what you could do differently to avoid it in the future.
Report Malware
If you think your computer has malware, the Federal Trade Commission wants to know.
File a complaint at www.ftc.gov/complaint.
Resources: OnGuardOnline.gov
Social Networking
Social networking sites such as Facebook, Twitter and LinkedIn have become extremely popular in recent years. They’re a great way to keep family and friends updated on your life and connect with colleagues and communities that share your interests. You can use social networks to build a positive online reputation.
The first step is STOP. THINK. CONNECT.
Protect Your Personal Information
Since social networking sites are about sharing, you may be prompted or tempted to reveal personal information.
Make sure you are comfortable with the information you share. Draw the line between what’s okay to share and what’s best kept private.
Secure your accounts
Ask for protection beyond passwords. Many account providers now offer additional ways for you verify who you are before you log into that site.
Make passwords long and strong
Combine capital and lowercase letters with numbers and symbols to create a more secure password.
Unique account, unique password: Separate passwords for every account helps to thwart cybercriminals.
Own your online presence
When available, set the privacy and security settings on websites to your comfort level for information sharing. It's ok to limit who you share information with.
Connect with Care
When you use social networks you are joining a global community. Therefore, it’s smart to approach social networking with a degree of caution. Remember that people may not be who they say they are. If one of your friend’s accounts is compromised, you could get spammy and suspicious posts.
When in doubt, throw it out
Links in tweets, posts, and online advertising are often the way cybercriminals compromise your computer. If it looks suspicious, even if you know the source, it's best to delete.
Get savvy about Wi-Fi hotspots
Limit the type of business you conduct and adjust the security settings on your device to limit who can access your machine.
Protect your $$
When banking and shopping, check to be sure the sites is security enabled. Look for web addresses with “https://” or “shttps://”, which means the site takes extra measures to help secure your information. “https://” is not secure.
Keep a Clean Machine
You can’t be safe and secure if the technology you are using is vulnerable.
Keep security software current
Having the latest security software, web browser, and operating system are the best defenses against viruses, malware, and other online threats.
Automate software updates
Many software programs will automatically connect and update to defend against known risks. Turn on automatic updates if that’s an available option.
Protect all devices that connect to the Internet
Along with computers, smart phones, gaming systems, and other web-enabled devices also need protection from viruses and malware.
Plug & scan
“USBs” and other external devices can be infected by viruses and malware. Use your security software to scan them.
Be a Good Online Citizen
Social networks work best when people maintain the same level of courtesy online as they would in the real world.
Safer for me more secure for all
What you do online has the potential to affect everyone – at home, at work and around the world. Practicing good online habits benefits the global digital community.
Know what action to take
If someone is harassing or threatening you, remove them from your friends list, block them, and report them to the site administrator.
Help the authorities fight cyber crime
Report stolen finances or identities and other cybercrime to www.ic3.gov (Internet Crime Complaint Center), the Federal Trade Commission at https://consumer.ftc.gov/ (if it's fraud), and to your local law enforcement or state attorney general as appropriate.
STOP. Before you use the Internet, take time to understand the risks and learn how to spot potential problems.
THINK. Take a moment to be certain the path is clear ahead. Watch for warning signs and consider how your actions online could impact your safety, or your family’s.
CONNECT. Enjoy the Internet with greater confidence, knowing you’ve taken the right steps to safeguard yourself and your computer.
Resources: StaySafeOnline.org and StopThinkConnect.org
Mobile Apps
If you have a smart phone or other mobile device, you probably use apps – to play games, get turn-by-turn directions, access news, books, weather, and more. Easy to download and often free, mobile apps can be so much fun and so convenient that you might download them without thinking about some key considerations: how they’re paid for, what information they may gather from your device, or who gets that information.
Questions About Your Privacy
What types of data can apps access?
When you sign up with an app store or download individual apps, you may be asked for permission to let them access information on your device.
- Some apps may be able to access:
- your phone and email contacts
- call logs
- internet data
- calendar data
- data about the device’s location
- the device’s unique IDs
- information about how you use the app itself
Some apps access only the data they need to function; others access data that’s not related to the purpose of the app.
If you’re providing information when you’re using the device, someone may be collecting it – whether it’s the app developer, the app store, an advertiser, or an ad network. And if they’re collecting your data, they may share it with other companies.
How can I tell what information an app will access or share?
It’s not always easy to know what data a specific app will access, or how it will be used. Before you download an app, consider what you know about who created it and what it does. The app stores may include information about the company that developed the app, if the developer provides it. If the developer doesn’t provide contact information – like a website or an email address – the app may be less than trustworthy.
If you’re using an Android operating system, you will have an opportunity to read the “permissions” just before you install an app. Read them. It’s useful information that tells you what information the app will access on your device. Ask yourself whether the permissions make sense given the purpose of the app; for example, there’s no reason for an e-book or “wallpaper” app to read your text messages.
Why do some apps collect location data?
Some apps use specific location data to give you maps, coupons for nearby stores, or information about who you might know nearby. Some provide location data to ad networks, which may combine it with other information in their databases to target ads based on your interests and your location.
Once an app has your permission to access your location data, it can do so until you change the settings on your phone. If you don’t want to share your location with advertising networks, you can turn off location services in your phone’s settings. But if you do that, apps won’t be able to give you information based on your location unless you enter it yourself.
Your phone uses general data about its location so your phone carrier can efficiently route calls. Even if you turn off location services in your phone’s settings, it may not be possible to completely stop it from broadcasting your location data.
Questions About Advertising
Why does the app I downloaded have ads in it?
Developers want to provide their apps as inexpensively as possible so lots of people will use them. If they sell advertising space in the app, they can offer the app for a lower cost than if it didn’t have ads. Some developers sell space in their apps to ad networks that, in turn, sell the space to advertisers.
Developers want to provide their apps as inexpensively as possible so lots of people will use them. If they sell advertising space in the app, they can offer the app for a lower cost than if it didn’t have ads. Some developers sell space in their apps to ad networks that, in turn, sell the space to advertisers.
Why do I see the ads I do?
Advertisers believe you’re more likely to click on an ad targeted to your specific interests. So ad networks gather the information apps collect, including your location data, and may combine it with the kind of information you provide when you register for a service or buy something online. The combined information allows the mobile ad network to send you targeted ads – ads that may be relevant to someone with your preferences and in your location.
Malware and Security Concerns
Should I update my apps?
Your phone may indicate when updates are available for your apps. It’s a good idea to update the apps you’ve installed on your device and the device’s operating system when new versions are available. Updates often have security patches that protect your information and your device from the latest malware.
Could an app infect my phone with malware?
Some hackers have created apps that can infect phones and mobile devices with malware. If your phone sends email or text messages that you didn’t write, or installs apps that you didn’t download, you could be looking at signs of malware.
If you think you have malware on your device, you have a few options: you can contact customer support for the company that made your device; you can contact your mobile phone carrier for help; or you can install a security app to scan and remove apps if it detects malware. Security apps for phones are relatively new; there are only a few on the market, including some with free versions.
Mobile App User Reviews
Can I trust all the user reviews I read about an app?
Most app stores include user reviews that can help you decide whether to download. But some app developers and their marketers have posed as consumers to post positive comments about their own products. In fact, the Federal Trade Commission recently sued a company for posting fake comments about the apps it was paid to promote.
Resources: OnGuardOnline.gov
Fake Check Scams
No matter the circumstances, don’t agree to deposit a check from a stranger and wire money back. If the check bounces, you’ll owe the bank any money you withdrew.
The Bait
You get a response to your ad or online auction posting offering to pay with a cashier's, personal, or corporate check. At the last minute, the so-called buyer (or the buyer's "agent") comes up with a reason for writing the check for more than the purchase price, and asks you to wire back the difference after you deposit the check.
The Catch
If you deposit the check, you lose. Typically, the checks are counterfeit, but they're good enough to fool unsuspecting bank tellers and increase the balance in your bank account – for a few days. But when the check eventually bounces, you are liable for the entire amount.
What You Can Do
Never accept a check for more than your selling price, no matter how tempting the plea or convincing the story. If the buyer sends the incorrect amount, return the check, and do not send the merchandise.
Consider using an online payment service instead; they often offer more protection for both you and the buyer. If you choose to accept checks, ask for a check from a bank with a local branch. That way, you can visit personally to make sure the check is valid. If that's not possible, call the bank that issued the check (don’t use a phone number given to you by the person who gave you the check). Ask if the check is valid.
Report Online Scams
If you believe you’ve responded to an online scam, file a complaint with:
- The Federal Trade Commission
- The FBI’s Internet Crime Complaint Center
- Your State Attorney General
Resources: OnGuardOnline.gov
Lotteries & Sweepstakes
Scam artists often use the promise of a valuable prize or award to entice people to send money.
The Bait
You get a letter or an email message that claims you’ve already won a foreign lottery or an online sweepstakes. The letter may be from a government agency, a bank, a well-known national company, or a company you never heard of. Regardless of the return address, the only thing between you and your winnings: a check or wire transfer from you to cover taxes, fees, shipping costs, or insurance.
The Catch
It’s illegal to play a foreign lottery. Any letter or email from a lottery or sweepstakes that asks you to pay taxes, fees, shipping, or insurance to claim your prize is a scam.
Some scammers ask you to send the money through a wire transfer. That’s because wire transfers are efficient: your money is transferred and available for pick up very quickly. Once it’s transferred, it’s gone. Others ask you to send a check or pay for your supposed winnings with a credit card. The reason: they use your bank account numbers to withdraw funds without your approval, or your credit card numbers to run up charges.
What You Can Do
An offer to play a foreign lottery can be tempting and fun, but it’s also illegal. If a sweepstakes run by an American company is legitimate, you won’t have to pay to enter or to win. That’s the law. No federal government agency runs or supervises a lottery; regardless, if you have to pay, it’s a purchase, not a prize.
Report Online Scams
If you believe you’ve responded to an online scam, file a complaint with:
The Federal Trade Commission
The FBI’s Internet Crime Complaint Center
Your state Attorney General
The FBI’s Internet Crime Complaint Center
Your state Attorney General
Resources: OnGuardOnline.gov
Texting Scam
Credit unions from around the country have reported their members are receiving bogus text message (smishing) alerts. The text message indicates it is from Credit Union Services and advises the member to click the link provided in the text message to have their card reactivated. This is a scam as no credit union would ever ask a member for this type of information using text messaging.
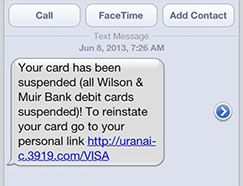
Telephone Scam
There are many types of phone call scams that attempt to steal debit card information.
It happens like this: A person receives a phone call at home, sometimes with the phone number of origin displaying as the homeowner's own number. The homeowner answers the phone and an automated message declares that there has been a security breach with their debit card. The message then prompts the homeowner to enter their debit card number on the phone’s keypad. THIS IS A SCAM, INTENDED TO STEAL YOUR ACCOUNT INFORMATION AND FUNDS.
If you receive a phone call similar to this – HANG UP! DO NOT enter your debit card number. L&N Federal Credit Union will NEVER ask you, or prompt you, for debit card or account information.
Other attempts have someone call and say they are with the credit union and say it is important for the member to give them their debit card number or checking account number, due to some problem or fraud risk.
Again, DO NOT EVER give your account numbers or debit card numbers to someone over the phone posing as a credit union employee. We will never ask that info because we already have it!
Smishing
Short for SMS Phishing, smishing is a variant of phishing email scams that instead utilizes Short Message Service (SMS) systems to send bogus text messages.
Smishing scams frequently seek to direct the text message recipient to visit a website or call a phone number, at which point the person being scammed is enticed to provide sensitive information such as credit card details or passwords. Smishing websites are also known to attempt to infect the person's computer with malware.
Like phishing, short message service (SMS) text messages, or “smishing,” makes consumers think their financial accounts may be compromised, and therefore they follow the fake URL or call a fraudulent phone number even if they suspect it is a scam. But identifying the scam is a consumer’s first defense from becoming a victim of the crime.
You should be wary of any message that comes from “5000″ or any other number that is not a cell number. A message that is asking you to respond quickly can be a scam, and you should stop and think it over before taking action.
If you are able to capture the telephone number used by the fraudster, report the number to the following organizations:
- The Federal Trade Commission at spam@uce.gov.
- The member’s landline or mobile phone carrier.
- The credit union’s local telephone carrier.
